Do not shop at Target. They are incompetent boobs. Their entire system was compromised. They are lying to you about your information being secure. Make them pay for their gross negligence.
A First Look at the Target Intrusion, Malware
http://krebsonsecurity.com/2014/01/a-first-look-at-the-target-intrusion-malware/
Last weekend, Target finally disclosed at least one cause of the massive data breach that exposed personal and financial information on more than 110 million customers: Malicious software that infected point-of-sale systems at Target checkout counters. Today’s post includes new information about the malware apparently used in the attack, according to two sources with knowledge of the matter.
In an interview with CNBC on Jan. 12, Target CEO Gregg Steinhafel confirmed that the attackers stole card data by installing malicious software on point-of-sale (POS) devices in the checkout lines at Target stores. A report published by Reuters that same day stated that the Target breach involved memory-scraping malware.
This type of malicious software uses a technique that parses data stored briefly in the memory banks of specific POS devices; in doing so, the malware captures the data stored on the card’s magnetic stripe in the instant after it has been swiped at the terminal and is still in the system’s memory. Armed with this information, thieves can create cloned copies of the cards and use them to shop in stores for high-priced merchandise. Earlier this month, U.S. Cert issued a detailed analysis of several common memory scraping malware variants.
Target hasn’t officially released details about the POS malware involved, nor has it said exactly how the bad guys broke into their network. Since the breach, however, at least two sources with knowledge of the ongoing investigation have independently shared information about the point-of-sale
malware and some of the methods allegedly used in the attack.
‘BLACK POS’
On Dec. 18, three days after Target became aware of the breach and the same day this blog broke the story, someone uploaded a copy of the point-of-sale malware used in the Target breach to ThreatExpert.com, a malware scanning service owned by security firm Symantec. The report generated by that scan was very recently removed, but it remains available via Google cache (Update, Jan. 16, 9:29 a.m.: Sometime after this story ran, Google removed the cached ThreatExpert report; I’ve uploaded a PDF version of it here).
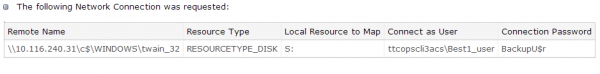
According to sources, “ttcopscli3acs” is the name of the Windows computer name/domain used by the POS malware planted at Target stores; the username that the malware used to upload stolen data data was “Best1_user”; the password was “BackupU$r”
According to a source close to the investigation, that threatexpert.com report is related to the malware analyzed at this Symantec writeup (also published Dec. 18) for a point-of-sale malware strain that Symantec calls “Reedum” (note the Windows service name of the malicious process is the same as the ThreatExpert analysis –”POSWDS”). Interestingly, a search in Virustotal.com — a Google-owned malware scanning service — for the term “reedum” suggests that this malware has been used in previous intrusions dating back to at least June 2013; in the screen shot below left, we can see a notation added to that virustotal submission, “30503 POS malware from FBI”.
The source close to the Target investigation said that at the time this POS malware was installed in Target’s environment (sometime prior to Nov. 27, 2013), none of the 40-plus commercial antivirus tools used to scan malware at virustotal.com flagged the POS malware (or any related hacking tools that were used in the intrusion) as malicious. “They were customized to avoid detection and for use in specific environments,” the source said.
 That source and one other involved in the investigation
That source and one other involved in the investigation
who also asked not to be named said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system.
According the author of BlackPOS — an individual who uses a variety of nicknames, including “Antikiller” — the POS malware is roughly 207 kilobytes in size and is designed to bypass firewall software. The barebones “budget version” of the crimeware costs $1,800, while a more feature-rich “full version” — including options for encrypting stolen data, for example — runs $2,300.
THE ATTACK
Target has yet to honor a single request for comment from this publication, and the company has said nothing publicly about how this breach occurred. But according to sources, the attackers broke in to Target after compromising a company Web server. Somehow, the attackers were able to upload the malicious POS software to store point-of-sale machines, and then set up a control server within Target’s internal network that served as a central repository for data hoovered by all of the infected point-of-sale devices.
“The bad guys were logging in remotely to that [control server], and apparently had persistent access to it,” a source close to the investigation told KrebsOnSecurity. “They basically had to keep going in and manually collecting the dumps.”
It’s not clear what type of software powers the point-of-sale devices running at registers in Target’s U.S. stores, but multiple sources say U.S. stores have traditionally used a home-grown software called Domain Center of Excellence, which is housed on Windows XP Embedded and Windows Embedded for Point of Service (WEPOS). Target’s Canadian stores run POS devices from Retalix, a company recently purchased by payment hardware giant NCR. According to sources, the Retalix POS systems will be rolled out
to U.S. Target locations gradually at some point in the future.
WHO IS ANTIKILLER?
A more full-featured Breadcrumbs-level analysis of this malware author will have to wait for another day, but for now there are some clues already dug up and assembled by Russian security firm Group-IB.
Not long after Antikiller began offering his BlackPOS crimeware for sale, Group-IB published an analysis of it, stating that “customers of major US banks, such as such as Chase (Newark, Delaware), Capital One (Virginia, Richmond), Citibank (South Dakota), Union Bank of California (California, San Diego), Nordstrom FSB Debit (Scottsdale, Arizona), were compromised by this malware.”
In his sales thread on at least one crime forum, Antikiller has posted a video of his product in action. As noted by Group-IB, there is a split second in the video where one can see a URL underneath the window being recorded by the author’s screen capture software which reveals a profile at the Russian social networking site Vkontakte.ru. Group-IB goes on to link that account to a set of young Russian and Ukranian men who appear to be actively engaged in a variety of cybercrime activities, including distributed denial-of-service (DDoS) attacks and protests associated with the hackivist collective known as Anonymous.
One final note: Dozens of readers have asked whether I have more information on other retailers that were allegedly victimized along with Target in this scheme. According to Reuters, “smaller breaches on at least three other well-known U.S. retailers took place and were conducted using similar techniques as the one on Target.” Rest assured that when and if I have information about related breaches I feel confident enough about to publish, you will read about it here first.




A Closer Look at the Target Malware, Part II
Brian Krebbs
Yesterday’s story about the point-of-sale malware used in the Target attack has prompted a flood of analysis and reporting from antivirus and security vendors about related malware. Buried within those reports are some interesting details that speak to possible actors involved and to the timing and discovery of this breach.
As is the case with many data breaches, the attackers in this attack used a virtual toolbox of crimeware to get the job done. As I noted in a Tweet shortly after filing my story Wednesday, at least one of those malware samples includes the text string “Rescator.” Loyal readers of this blog will probably find this name familiar. That’s because Rescator was the subject of a blog post that I published on Dec. 24, 2013, titled “Who is Selling Cards from Target?“.
In that post, I examined a network of underground cybercrime shops that were selling almost exclusively credit and debit card accounts stolen from Target stores. I showed how those underground stores all traced back to a miscreant who uses the nickname Rescator, and how clues about Rescator’s real-life identity suggested he might be a particular young man in Odessa, Ukraine.
This afternoon, McAfee published a blog post confirming many of the findings in my story yesterday, including that two malware uploaders used in connection with the Target attack contained the Rescator string:
“z:\Projects\Rescator\uploader\Debug\scheck.pdb”.
Earlier this morning, Seculert posted an analysis that confirmed my reporting that the thieves used a central server within Target to aggregate the data hoovered up by the point-of-sale malware installed at Target. According to Seculert, the attack consisted of two stages.
“First, the malware that infected Target’s checkout counters (PoS) extracted credit numbers and sensitive personal details. Then, after staying undetected for 6 days, the malware started transmitting the stolen data to an external FTP server, using another infected machine within the Target network.”
Seculert continues: “Further analysis of the attack has revealed the following: On December 2, the malware began transmitting payloads of stolen data to a FTP server of what appears to be a hijacked website. These transmissions occurred several times a day over a 2 week period. Also on December 2, the cyber criminals behind the attack used a virtual private server (VPS) located in Russia to download the stolen data from the FTP. They continued to download the data over 2 weeks for a total of 11 GBs of stolen sensitive customer information. While none of this data remains on the FTP server today, analysis of publicly available access logs indicates that Target was the only retailer affected. So far there is no indication of any relationship to the Neiman Marcus attack.”
Target has taken quite a few lumps from critics who say the company waited too long to disclose the breach, and new details about when it may have known something was wrong are likely to fan those flames. As I wrote yesterday, the point-of-sale malware used in Target referenced a domain within Target’s infrastructure called “ttcopscli3acs”. Several sources, including Seculert’s Aviv Raff and Dmitri Alperovitch at CrowdStrike, searched for other files with that unique string within the corpus of malware uploaded to Virustotal.com, a service that employs more than 40 commercial antivirus tools to produce reports about suspicious files submitted by users.
That search turned up numerous related files — including the aforementioned malware uploaders with Rescator’s nickname inside — all dated Dec. 11, 2013. Since this malware is widely thought to have been custom-made specifically for the Target intrusion, it stands to reason that someone within Target (or a security contractor working at the company’s behest) first detected the malware used in the breach on that date, and then submitted it to Virustotal.
Yesterday’s story cited sources saying the malware used in the Target breach was carefully crafted to avoid detection by all antivirus tools on the market. These two virustotal scan results from Jan. 16 (today) show that even to this day not a single antivirus product on the market detects these two malicious files used in the Target attack. Granted, the antivirus tools used at virustotal.com do not include behavioral detection (testing mostly for known threat signatures). I point it out mainly because nobody else has so far.
Incidentally, in malware-writer parlance, the practice of obfuscating malware so that it is no longer detected by commercial antivirus tools is known as making the malware “Fully Un-Detectable,” or “FUD” as most denizens of cybercrime forums call it. This is a somewhat amusing acronym to describe the state of a thing that is often used by security industry marketing people to generate a great deal of real-world FUD, a.k.a. Fear Uncertainty and Doubt.
“Malicious software that infected point-of-sale systems at Target checkout counters”
———— from the article
Today, it’s Target.
Who will it be tomorrow? Sears? JCP? Home Depot? YOU, the consumer, are at risk EVERY time you swipe your credit card. Just a matter of time.
Get rid of every credit card you own. If not possible, have no more than one, or two, maximum. That at least reduces your risk and makes it easier to check your statement …. EVERY day (as Ms Freud does … identity theft will change your life.)
Also consider getting a Credit Freeze.
Works like a charm …. against someone obtaining NEW credit in your name.
About three weeks ago Ms Freud got a new car, Hyundai Sonata. It’s in the driveway. This morning the dealership called. The bank still can’t run the credit report … and can’t determine /verify the agreed upon payment. Ha!
Ms Freud “froze” the credit several years ago after a serious identity theft wiped out the checking account. They gave her a “pin” number so she can unlock it as needed. Of course, she lost it. We’ve spent the last three weeks trying to get it unlocked. She has over-nighted copies of her drivers license, soc sec card, bank statements, and utility bills. I think the next step is to submit DNA. As of this morning we were told by one of the credit bureaus that it would be another 7 – 10 business days before they’ll send a new pin number via snail mail. Don’t lose your P.I.N.!!!
There is a supersize Target near my house. Last weekend I went into it to purchase a fan for my office. I paid cash.
I’ve really tried to use only cash the past few months, but I did lapse and use my credit union debit card at Target on the weekend in question.
Target has given me a year of free credit monitoring and my credit union just issued me a new debit card.
I figure if anybody surreptitiously examines my finances, they will not be interested in stealing my identity.. Perhaps they’re welcome to it?
Don’t give Target your Social Security number
“Trust no one,” experts say, not even fraud investigators
By Quentin Fottrell
After announcing the massive credit-card breach, Target (NYSE:TGT) warned customers against giving out their Social Security number, driver’s license number and other personal details to fraudsters trying to profit from confusion and anxiety over the news. But what if Target itself wants your social security number?
On Wednesday, one Target customer received a call from the Target fraud-detection department about a suspicious $1,200 transaction on his store credit card. But Michael Baxter, from Sommerville, Mass., says he was surprised by the depth of confidential information the company asked him to fork over — and wondered if it was a scam. Target emailed him a fraud-investigation questionnaire requesting information such as his Social Security number, driver’s license number, phone number, credit card number, address and even his children’s names. “I told them they were insane to be expecting this information,” he told CBS News in Boston .
Target later said the disclosure wasn’t necessary. “Our policy is to investigate all fraud claims even if the form is not filled out, and filling out the form is not a requirement,” it said in a statement. “However, if we don’t have the form filled out, it makes our investigation more difficult.”
Some consumer advocates disagree. “With all due respect to Target, I’m not sure how it makes their job more difficult,” says John Ulzheimer, a credit expert at CreditSesame.com, a firm that provides online credit and debt analysis to consumers. Companies should never ask for a full social security number or driver’s license, they should confirm your card number, zip code and one or two security questions. To set up a store card in the first place, Target should have all that information on file already, Ulzheimer says, and asking customers for that information is merely a time-saving shortcut.
“The Target form was total overkill,” says Adam Levin, co-founder of online security company Identity Theft 911. “When a consumer is a victim of identity theft or fraud, the last thing you do is pressure them to give you more information.” To be sure, Target’s credit-card agreement requires customers to “ comply with the procedures ” it may require for its investigation. But other forms, like this Navy Federal Credit Union affidavit of fraud, doesn’t ask for the consumer’s social security number, Levin says.
Assume every call is a phishing scam, experts says. Consumers should never give out personal details over the telephone, even if the caller seems to represent Target or the email appears to be from a Target email address. “Consumers need to be careful whenever they are contacted by an unsolicited caller,” says Linda Sherry, director of national priorities at Consumer Action. Hang up and call the number on your card. Target itself warns against “phishing” scams — calls, emails or text messages that appear to offer protection, but are actually trying to get more personal information from customers.
Bottom line: “Don’t share any information with organizations that they don’t absolutely require,” says Chester Wisniewski, senior security adviser at Sophos, an online security consultancy. There is no federal legislation governing what information a consumer can withhold in the event of a data breach and it typically depends on the agreement signed. In the meantime, Wisniewski says, “trust no one.” A supermarket or coffee shop wants your birth date and zip code for their frequent shopper card? Choose Jan. 1. and 90210, Wisniewski suggests. “Thousands of security experts were born on Jan. 1,” he says.
The parent company of the Chuck. E. Cheese restaurant chain has agreed to be acquired by an affiliate of Apollo Global Management for $1.3 BILLION
This is what I know about Chuck E Cheese
I took my kids there once, about 20 years ago. Yes, the kids enjoyed the games. But, the pizza smelled bad and tasted awful. Worst chain-pizza ever. Even worse than frozen pizza. Never went back, ever.
Since some douchnozzles thought this chain is worth a billion dollars, maybe I should give it one more shot?
A 17-year-old is reportedly author behind malware that led to Target’s data breach
The data breach that has gotten many consumers skittish about using their cards and hurt retailer Target Corp.’s TGT reputation and sales may be traced to a 17-year-old Russian who authored the malware used in the security breach, according to a cyber-intelligence firm.
IntelCrawler, based in Los Angeles, said the close-to-17-year-old Sergey Taraspov is a well-known programmer of malicious code in the underground world. The cyber intelligence firm added the BlackPOS malware is an inexpensive “off the shelf” malware, which it said may also have been involved in the Neiman Marcus attack. It said it has uncovered six other breaches though it didn’t respond to MarketWatch requests seeking to identify the names of the other retailers.
“He is still visible for us, but the real bad actors responsible for the past attacks on retailers such as Target and Neiman Marcus were just his customers,” said Dan Clements, the company’s president, on its website.
IntelCrawler said BlackPOS first infected retailers’ systems in Australia, Canada and the U.S. It said the malware, which first carried the name of “Kaptoxa,” or potato, in Russian slang before being renamed, has been sold to cybercriminals in Eastern Europe and other countries, including owners of underground credit-card shops.
Separately, iSight Partners, working with the U.S. Secret Service, said the Kaptoxa software has potentially infected “a large number of retail information systems.”
The Target attack has potentially compromised 40 million card accounts with some 70 million shoppers’ email and other personal information also stolen from a separate system during the security breach. Neiman Marcus has said it doesn’t have a specific number of consumers being affected.
– Andria Cheng
17 years old.When I was 17 I would have been ridding around in my 1972 Chevy or out side .I was always doing things with high school buddies.Now,a lot kids just stay in their rooms and develop malicious things to deliberately hurt other people.
“The cyber intelligence firm added the BlackPOS malware …..” —- from the article
BlackPOS?? So … Obama did it?
2014-01-17 08:23 by Karl Denninger
On The Retail Data Hack
The so-called Target hack is much more than you’re being told.
First, it has come out that the code apparently was written in Russia. This does not surprise me one bit, given what I’ve seen over the last couple of decades. Indeed, going back to the late 90s and into the 2000s this particular part of the world has been known as a hotbed of financial rip-offs centered in, but not limited to, the credit card and identity-theft business.
I have a working theory on this that I cannot yet validate, but if I’m right, and it is looking increasingly likely that I am, you’re going to utterly shocked when you find out how far this goes, and how bad it is.
It is already known that the original attempts to downplay this — that it only hit the company starting at a given time late in the year, that it was a “scrape” of POS terminals at the time of purchase, and thus the impact was (at least a bit) limited is utter and complete horsecrap. That has been proved by the revelations that we’ve already had come into the public.
We’ll see if the rest of my working assumptions prove up — I need one or two more solid data points that are irrefutable in some form or fashion (e.g. someone’s admission) before I’m willing to stick my neck out in public on exactly what happened and how, but if I’m right this is much, much worse than anyone is letting on, and in addition it’s also not over by any stretch of the imagination either, despite what both the government and retailers would love for you to believe.
Further, this demonstrates that these firms are not, in any material way, operating secure internal networks.
They can claim otherwise all they’d like but the fact of the matter is that a hack of this sort proves such claims false.
I find it satisfying deep down in my soul that after being told for several decades about how great a cash free, digital money only economy would be and how behind the times us cash only folks were, that the whole thing is just another lie.
Take your money out of the bank as soon as you are payed and stuff your mattress.